Has a vendor or contractor asked your city to change the way they are paid? Did they ask to be paid with an electronic funds transfer or an automated clearing house (ACH) transfer instead of a physical check as originally agreed upon? There is a chance you may be paying an impostor using a technique called phishing.
What is phishing?
Phishing is an online scam that targets people, businesses and agencies through messages sent via email, text or direct message that appear to be from a reputable source. Phishing messages commonly ask for personal identifying information that is then used to invade existing accounts. In what is commonly called spear phishing, an attacker may use information about a real company and its employees to make their messages even more persuasive and realistic.
Over the past several years, international scammers have successfully targeted numerous cities using phishing techniques, diverting large payments from city projects. Some of the losses are staggering, and the chances of recovery are almost zero.
Arlington, Massachusetts: $445,945.73
In 2020, perpetrators posing as a vendor used phishing, spoofing, social engineering and compromised email accounts to commit wire fraud totaling $445,945.73 meant for an Arlington High School building project.1https://statescoop.com/massachusetts-town-loses-445000-email-scam/
Cottage Grove, Minnesota: more than $1.2 million
In 2021, a $3.5 million contract for a sewage treatment project in the city’s south district was finalized with a local company. Over the next three months, almost half of that sum was sent to phishing scammers.2https://ca.news.yahoo.com/heres-city-minnesota-sent-phishing-010338800.html
Memphis, Tennessee: more than $773K
The city paid $773,695.45 in February 2022 to phishing scammers posing as a local construction company that had existing city contracts. The incident was not made public until June of 2024.3https://wreg.com/news/investigations/city-of-memphis-lost-773k-in-phishing-scam/
Fort Lauderdale, Florida: $1.2 million
Scammers duped the Florida city out of $1.2 million in September 2023. The city paid the sum after receiving what was believed to be a legitimate invoice from the construction company hired to build a new police station.4https://www.usatoday.com/story/news/nation/2023/09/25/scammers-dupe-fort-lauderdale-florida/70959727007/
Greater Sudbury, Ontario: more than $1.5 million
The Canadian city is trying to recover more than $1.5 million swindled in 2023 by fraudsters who allegedly infiltrated the email accounts of a construction company contracted to build an affordable housing project.5https://www.thestar.com/news/investigations/how-scammers-tricked-a-northern-ontario-city-into-wiring-1-5-million-to-a-toronto/article_482866d6-bfa7-11ee-a62c-fb332125fdc6.html
Gooding, Idaho: $1,092,519
In 2024, the city intended to pay a contractor hired to work on a wastewater project, but scammers were able to intercept and divert $1,092,519 of the city’s payments.6https://idahonews.com/news/local/city-of-gooding-loses-over-1-million-in-social-engineering-scam
Fresno, California: $613,737 loss spurs grand jury investigation
A Fresno County Civil Grand Jury investigation following a phishing attack on the city offers details of how these international organized crime rings target cities.7https://www.fresno.courts.ca.gov/system/files/general/grand-jury-report-3.pdf
- Construction began on a new police substation in southeast Fresno in April 2019, according to the grand jury report. The contractor requested to be paid by physical checks.
- The Fresno Finance Department received an email in January 2020 from the perpetrator of the scam who identified as an employee of the construction company. They asked to receive payments through an ACH transfer instead. In the following weeks, the department authorized two electronic payments to the perpetrator totaling $613,737.
- “At no time did the perpetrators submit fraudulent invoices,” the grand jury report said. “It appears they simply scoured the internet for large construction contracts being awarded by local governments. Using real data gleaned from the City Council agendas and minutes, they were able to identify this particular contract, used what information was publicly available, and initiated a successful phishing scheme on unsuspecting city employees.”
- The report revealed city staff failed to pick up on the fraud despite numerous signs. The fraudulent email addresses ended in “.us” while the contractor’s had ended in “.com”, and the scammers gave multiple bank account numbers across different states.
- The city learned about the scam when the construction company threatened to walk off the job over lack of payment.
- The grand jury found that finance department employees had failed to follow policies that would have prevented the fraud. The staff had not authenticated the ACH form to ensure that the “form submitted by the vendor [was] actually from the vendor of record.”
- They had also neglected to have a different staff member review the transfer, a step that was required for all “large disbursements.”
- The grand jury found that the electronic payment procedure was “largely unwritten at the time of the incident.”
- According to the grand jury’s report, “Training for the handling of these important money transfers was conducted verbally, and it appears that not all Finance Department employees were properly trained.”
- “Without strict observation and enforcement of new and existing internal controls,” it adds, “there is a high probability of similar losses in the future.”
Train now or pay later
Now is the time to review your municipal finance department’s policies and to train staff on recognizing phishing scams and the importance of reporting all suspected attacks to your information technology department. Even well-meaning and hard-working staff can be tricked by these sophisticated bad actors. Knowing how to spot the red flags in an email, text or direct message can help stop scammers before they get their hooks in your organization.
How to spot a phishing attempt
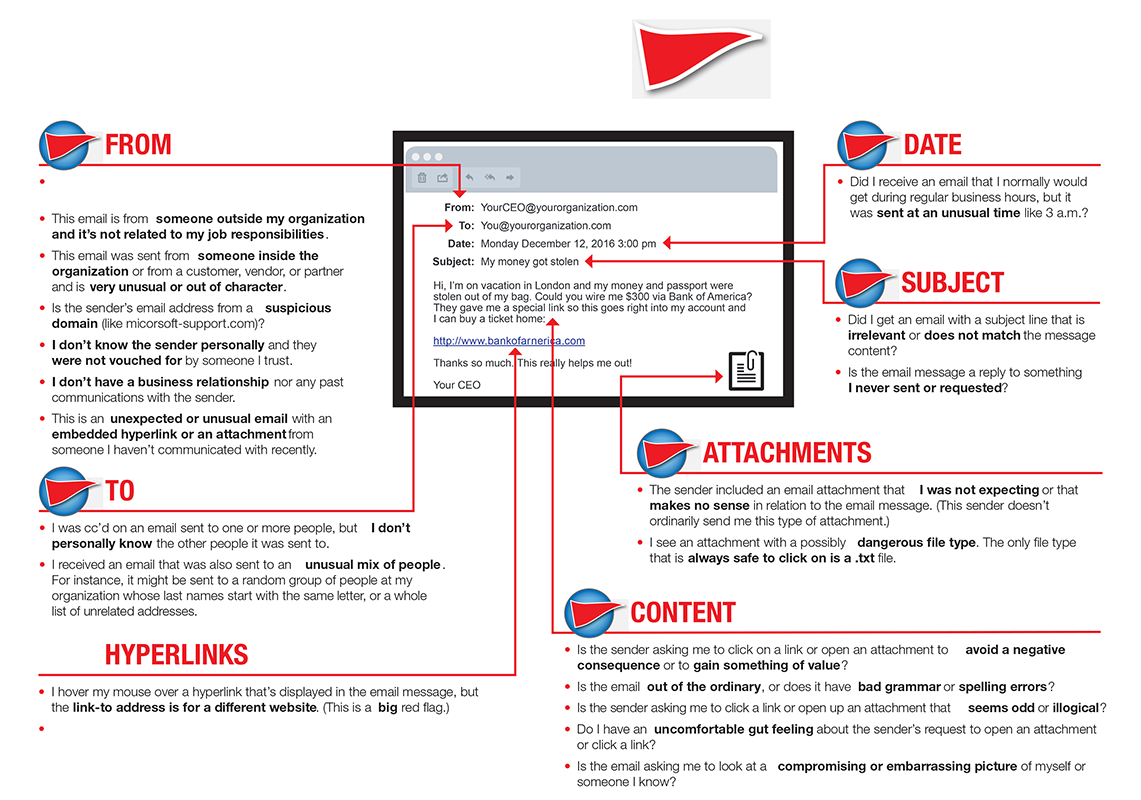
- Check the “From” email address Make sure to cross-check the email domain on any suspicious email. The sender’s email address should match the name and company in the signature of the email.
- Watch for misspellings and incorrect grammar Misspelled words and names, incorrect grammar and strange sentence construction are all red flags.
- Hyperlinks: Hover, don’t click If a message includes a hyperlink, don’t immediately click on it. Hover over the link to check if the URL leads to the website you would expect based on the sender.
- Be wary of attachments Do not open any attachment until you are absolutely certain the sender is legitimate.
- Beware of claims of urgency Rewards or scare tactics are two common phishing approaches that demonstrate a sense of urgency to get you to click faster.
- Don’t provide personal information Legitimate companies will never ask for sensitive or personal information over email.
- Check the time and date View with caution any emails that land in your inbox outside of normal business hours.
- Go with your gut Is the email about money or log-in information? Are you sure they are who they say they are? If you have even the smallest gut feeling that the email is not legitimate—even if you can’t exactly articulate why you feel that way—ask your IT team.
- 1
- 2
- 3
- 4
- 5
- 6
- 7